Problem
"There seem to be a few more files stored on the flash card server but we can't login. Can you?"
Solution
The site appears to be the same as the previous flaskcard challenges Flaskcards Skeleton Key and Flaskcards.
When we create an account, we are presented with the following screen: 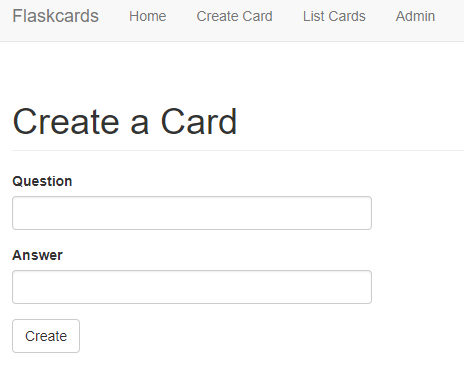
We can try server side injection. If we type in {{1+1}}, the webpage displays 2. Any values in double brackets is being executed on the server. After trying to find hidden variables, such as config, flag, etc; I decided to look for a remote code execution vulnerability.