Challenge
A good Hacker should always take good notes!
nc chall.pwnable.tw 10102
We are also provided a binary and the libc used on the server.
Solution
When running the binary, we can see four options:
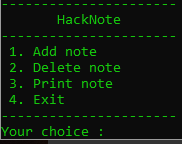
Understanding the binary
When reversing the binary, we can use the shown options to help identify functions used. I reversed the binary in Ghidra, and the following are the cleaned up decompilation output from the binary.